Access Control Policies
Often, especially when engineering small standalone or monolith applications, we ended up coupling our Identity Access Management (IAM) to our domain.
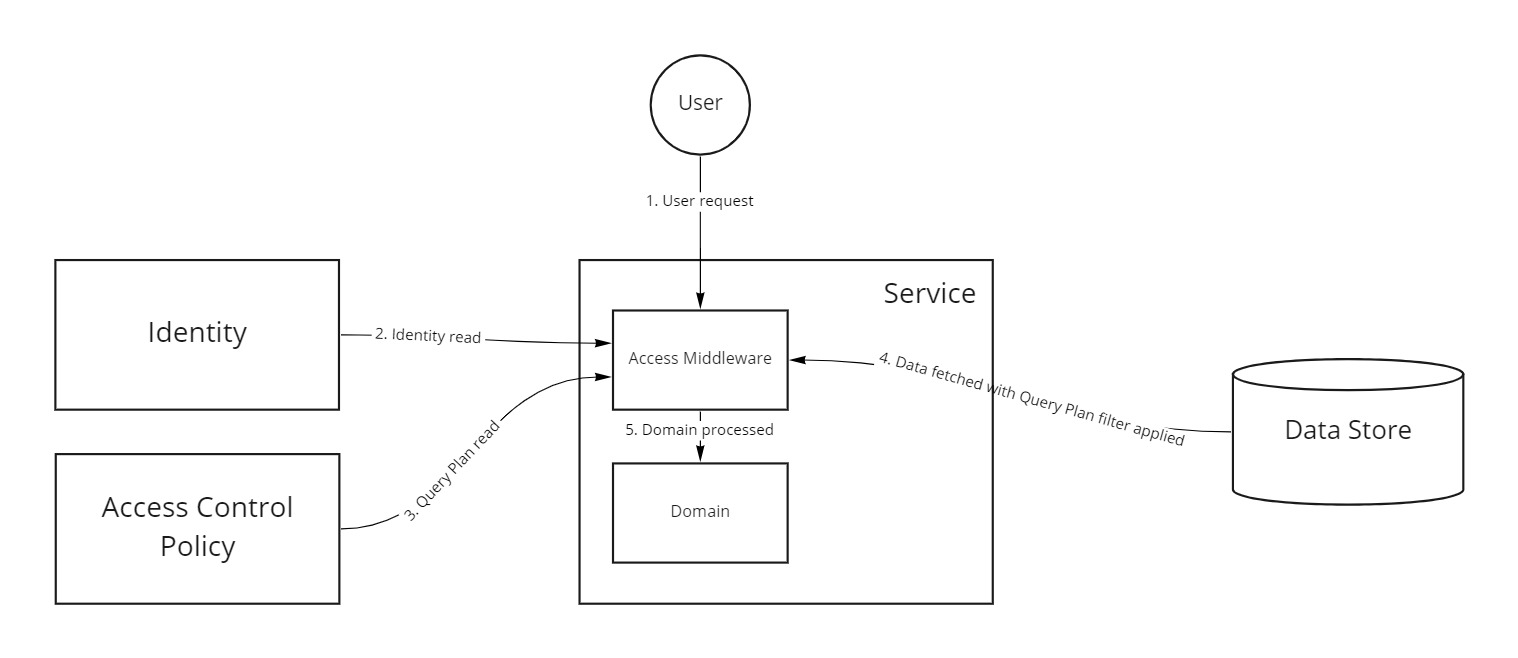
In a small-service ecosystem that is arranged according to business domains, identity sits in its own domain (and thus service), and access control operates on within the context of the identity and domain resource.
Typically, each service takes the identity and applies code-level access control - that is, determining whether an identity can -or cannot- do an action within code. This, unfortunately, couples our code with access control that, while easy for simple applications, spirals into complex code at scale.
The solution is to use an Access Control Policy (ACP) service to determine access outside your code. The ACP, when passed the identity and resource, can resolve access and either allow or deny the request.
Access Control at Source
In order to know if an identity has access to a resource, we need the identity and the resource first, then call our access control service to check if the identity is allowed to access the resource, right?
$resource = $repository->find(1);
$identity = $identityService->currentUser();
$accessControl->check($identity, $resource);

Well, yes, you can do it that way, but what if we could ask our access control service for a set of filters we could directly apply to our query to fetch the resource?
$identity = $identityService->currentUser();
$plan = $accessControl->check($identity, 'resource_name');
$resource = $repository->find(1, $plan);
This is Access Control at Source. In this situation, any user will only ever have access to the resources it’s allowed to access, as resources the user doesn’t have access to will never be returned from the datasource. Applying access control at the data-layer query time allows the application service to decouple itself from access control by not requiring hard checks in code, as well as high data security as actors will never be able to retrieve data that they do not have permission to access.